Access with SSH¶
Secure Shell (SSH) is the main command-line remote login tool in the Linux world. All UTHPC command-line based services provide SSH access for users.
Starting to use SSH requires three main steps:
- Verifying that an SSH client is installed on your computer.
- Creating a public and private SSH key pair.
- Using the client to connect to a remote SSH server.
The most recent versions of both Windows 10 and Windows 11 include a native SSH server and client, utilizing the OpenSSH framework, which facilitates remote sign-ins using the SSH protocol.
Verify OpenSSH Installation¶
Ensure that the OpenSSH client feature is installed on your Windows machine. If not, you can add it through the Windows Features menu.
- Open the "Settings" app.
- Go to "Apps" and then "Optional Features."
- Look for "OpenSSH Client" in the list. If it's not installed, click "Add a feature" and select "OpenSSH Client." Click "Install."
How to SSH into the Server¶
To SSH into a remote server, use the ssh command followed by the server's IP address or domain name and your username:
ssh username@server_ip_or_domain
username with your username on the remote server and server_ip_or_domain with the actual IP address or domain name of the server you want to connect to. You may be prompted to enter your password. Once you provide the correct credentials, you'll be connected to the remote server.
Generating an SSH key-pair¶
For added security and convenience, you can set up SSH key authentication.
-
Generate an SSH key pair using the
ssh-keygencommandssh-keygen -t ed25519- When prompted to choose the location to store the key, it is recommended to use the default location (typically
C:/Users/<username>/.ssh/ed25519). -
When prompted to enter a passphrase you may consider entering one for stronger security, but it is also OK to leave it empty.
Please make sure which rules apply in your institute, because in some institutes the use of a passphrase is MANDATORY. If you use a passphrase, it should be different from the password you use to log in to your ut.ee account and the UTHPC server.
- When prompted to choose the location to store the key, it is recommended to use the default location (typically
-
After generating the keys, you will find two files in your .ssh directory:
ed25519anded25519.pub. The.pubfile is your public key and the other file without extension is your private key:Mode LastWriteTime Length Name ---- ------------- ------ ---- -a---- 21/12/2023 2:55 PM 464 ed25519 -a---- 21/12/2023 2:55 PM 103 ed25519.pub -
To use the ssh key that was created above, the content of public key needs to be placed on the server into a text file
~/.ssh/authorized_keys. Copy the contents ofid_rsa.pub. In Command Prompt, you can usemore <path to file>, and in PowerShell, you can usecat <path to file>to view the file's contents.
The most recent versions of both Windows 10 and Windows 11 include a native SSH server and client, utilizing the OpenSSH framework, which facilitates remote sign-ins using the SSH protocol.
Verify OpenSSH Installation¶
Ensure that the OpenSSH client feature is installed on your Windows machine. If not, you can add it through the Windows Features menu.
- Open the "Settings" app.
- Go to "Apps" and then "Optional Features."
- Look for "OpenSSH Client" in the list. If it's not installed, click "Add a feature" and select "OpenSSH Client." Click "Install."
Generating an SSH key-pair¶
- Generating an SSH key pair can be done via Windows PowerShell. Please see the instructions in the relevant section.
- To use the created SSH key, you need to copy the public key to the remote server. To do so, you will first have to connect to the server. This process starts with installing WSL.
Installing WSL¶
Check System Requirements¶
Ensure you have Windows 10 or a more recent version of Windows. If you are using an older Windows version please see the manual install page.
Installation¶
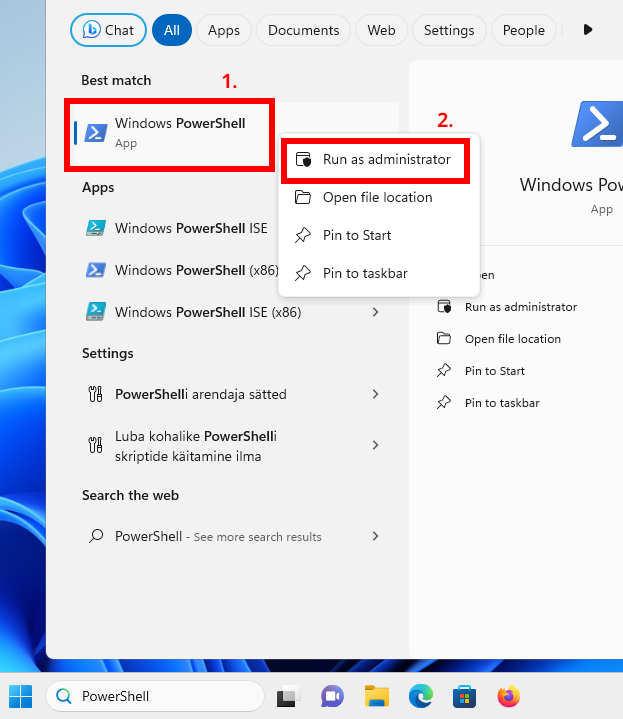
- Open PowerShell or Windows Command Prompt in administrator mode by right-clicking and selecting
Run as administrator. - Enter the command
wsl --install
- Restart your machine.
- After the restart a window titled "ubuntu" should open automatically.
- Enter your preferred username and password.
Info
Password characters will not be visible for security reasons. Dont worry they are there.
Update and Upgrade¶
After setting up your user, it's a good practice to update the package list and upgrade installed packages:
sudo apt update && sudo apt upgrade
Changing the default Linux distribution installed¶
By default, the installed Linux distribution will be Ubuntu. This can be changed using the -d flag. To change the distribution installed enter: wsl --install -d <Distribution Name>. (Replace <Distribution Name> with the name of the distribution you would like to install.)
To see a list of available Linux distributions available for download through the online store, enter: wsl --list --online or wsl -l -o. To install additional Linux distributions after the initial install, you may also use the command: wsl --install -d <Distribution Name>.
Using WSL to SSH into a Server¶
Open WSL¶
You can open WSL by searching for the Linux distribution you installed (e.g., "Ubuntu") in the Start menu or running wsl from the Command Prompt or PowerShell.
SSH into the Server¶
To SSH into a remote server, use the ssh command followed by the server's IP address or domain name and your username:
ssh username@server_ip_or_domain
Replace username with your username on the remote server and server_ip_or_domain with the actual IP address or domain name of the server you want to connect to.
You may be prompted to enter your password. Once you provide the correct credentials, you'll be connected to the remote server.
Now, you should be able to use WSL to SSH into a server running Linux. Make sure you have the necessary permissions and credentials to access the remote server.
Getting PuTTY and PuTTYgen¶
Download PuTTY from: www.putty.org .
It's enough to download and install PuTTY, since it comes bundled with PuTTYgen. After installing PuTTY, one can search for PuTTY and PuTTYgen on their computers.
Basic PuTTY usage¶
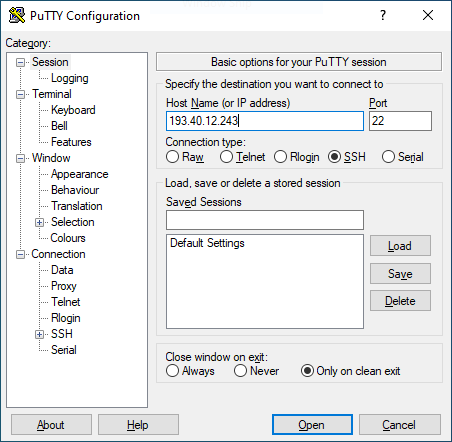
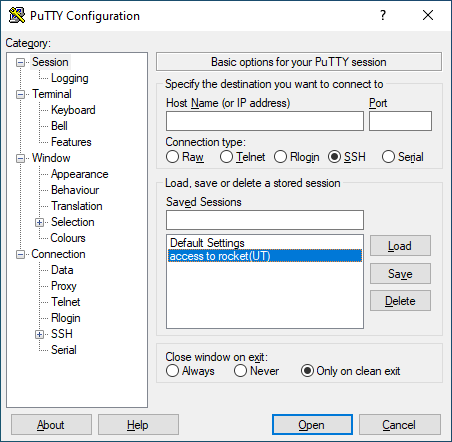
Into the slot of ’Host Name (or IP address)’ one must enter the IP address of the machine one is trying to connect to. When the machine in use has a resolvable name in a DNS server available to the world, one can also use the fully qualified domain name (FQDN) instead.
In the adjacent slot one must specify the Port your destination machine is expecting the ssh connection from. In a standard setup that port number is 22.
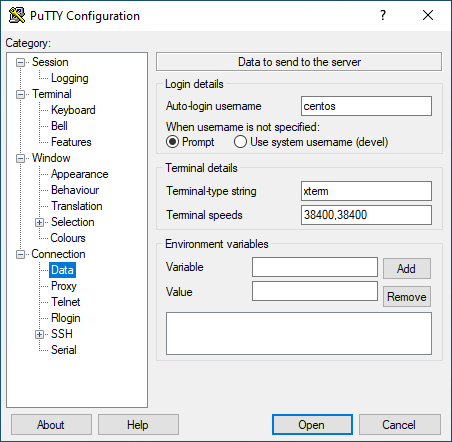
Accessing a machine with ssh requires one to specify the user name with which one can access the machine. One can automate the insertion of user name by choosing the Data tab in the left menu and specifying the user name one wished to use for the automatic user name insertion. In the following illustration, the username for the ’Auto-login username’ is centos.
In general the machines available from University of Tartu ETAIS interface. The default usernames are the following:
- Ubuntu-based image's default user is
ubuntu - Debian-based image's default user is
debian - CentOS-based image's default user is
centos - Windows-based image's default user is
Admin - typically your university (or ETAIS ) username for non-OpenStack machines.
After entering the desired username one can click ’Open’ and connect to the machine.
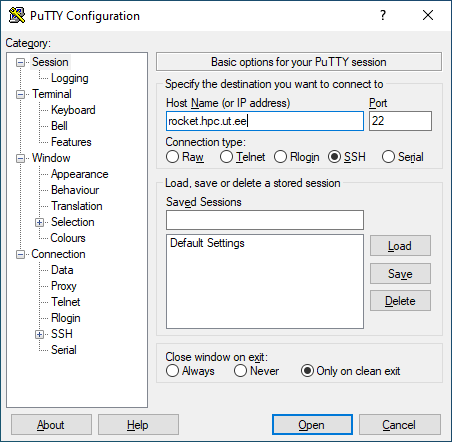
In order to save said username one can go back to the ’Session’ tab on the left hand side make sure the ’Host Name (or IP address)’ and ’Port’ are correct and then name the session something meaningful in the slot under ’Saved Sessions’ and click ’Save’ on the right hand side. The session parameters are now saved for future use.
When the user later returns to PuTTY one doesn't have to enter the username again in the ’Data’ tab on the left hand side, simply choosing the previously saved session form the list, in the example below that would be ’access to rocket (UT)’, and pressing the ’Load’ button the session parameters get loaded in and by pressing the ’Open’, PuTTY creates a new session to the desired machine with all the parameters already set by the loaded session.
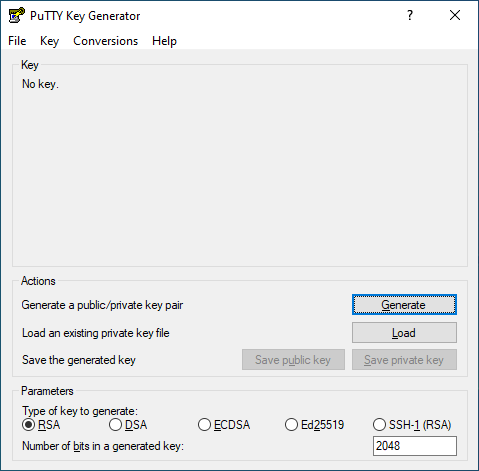
Generating public and private keys with PuTTYgen¶
Open PuTTYgen and click ’Generate’.
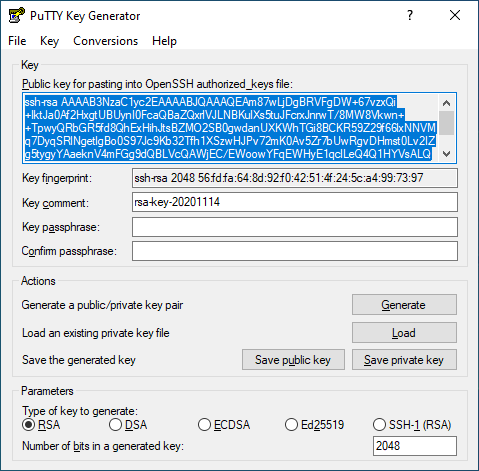
PuTTYgen instructs the user to move their mouse around in the white box to generate the key-pair. After the generation, PuTTYgen displays the pre-selected Public key in OpenSSH format. One should copy previously mentioned selection into a file. Using Notepad to save the public key is fine, the file format isn't important as long as the content of the public key stays intact.
After saving the public key, one must save the private key by clicking on the ’Save private key’ button.
After clicking the ’Save private key’ button one must save choose the location for the private key. Private key is the most important part of the public-private key pair, keeping it secure is of the utmost importance. The private key is with the .ppk file extension that's suitable for PuTTY.
To summarize the creation of public-private key pair, the format of the public key is in accordance to the OpenSSH standard and the private key is in the PuTTY format.
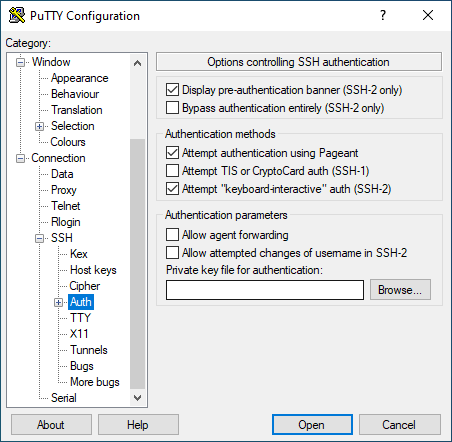
To fully automate the logging into a machine, one must load up a previously created session, go to the ’Auth’ tab on the left hand side and click ’Browse’. Locate the previously saved private key with the ’.ppk’ file format and choose ’Open’.
One should now go back to the ’Session’ tab in the left hand side and click the ’Save’ button again. Now the saved session uses the previously designated username, designated host with correct port and load up the specified private key, granting user access to the desired machine with least effort. Previous sentence does imply that one has appended the OpenSSH format public key to the desired host, usually into ~/.ssh/authorized_keys file, or in the case of ETAIS , one has added the public key under the SSH keys in ETAIS .
Copy Your Public Key to the Remote Server¶
On the remote server, accessed from the local Windows client, follow these steps to add your public key:
-
Connect to the remote Linux server using a WSL session or a standard password-protected PuTTY session, depending on your previous choice, and log in. NB! You can only ssh into
rocket.hpc.ut.eefrom within the university network or via the University of Tartu VPN. -
Create a directory named
~/.sshusing the command:mkdir ~/.ssh -
Set appropriate permissions for the
.sshdirectory with the command:This grants the user (owner) read, write, and execute permissions.chmod 700 ~/.ssh -
Create an empty text file named
authorized_keysusing the command:Paste the contents of the "Public key for pasting into OpenSSH authorized_keys file" into the text file. Confirm that the key is pasted correctly. Save and close the file.nano ~/.ssh/authorized_keys -
Secure the permissions of the
authorized_keysfile:This setting provides the user with read and write permissions on thechmod 600 ~/.ssh/authorized_keysauthorized_keysfile. -
Exit the SSH connection:
This closes the SSH connection.exit -
Attempt to log in using the SSH key:
Ensure successful login without requiring a password.ssh your_username@your_server_ip
By following these steps, you have securely added your public key to the remote server, allowing passwordless authentication using SSH keys.
Security¶
If your account password has been compromised, please do the following:
- Change your password immediately.
- Generate new SSH keys.
- Remove any old SSH keys from the server to prevent unauthorized access.
Taking these steps will help secure your account and protect your data.