vault.hpc.ut.ee¶
vault.hpc.ut.ee is UTHPC center's central dynamic security provider. It hosts credentials and information about systems.
For non-administrator users, this is mainly used by UTHPC administrators to share sensitive information with users of services, or by users to easily send sensitive data to UTHPC staff.
You can access Vault by going to https://vault.hpc.ut.ee , and logging in with the method ’LDAP’ and your University username and password.
Another option for power users is to download and install the vault binary into your machine, and use it over the command line.
How-to…¶
Following are few paragraphs how to use the Vault service, and utilize it for different purposes.
Access personal credentials¶
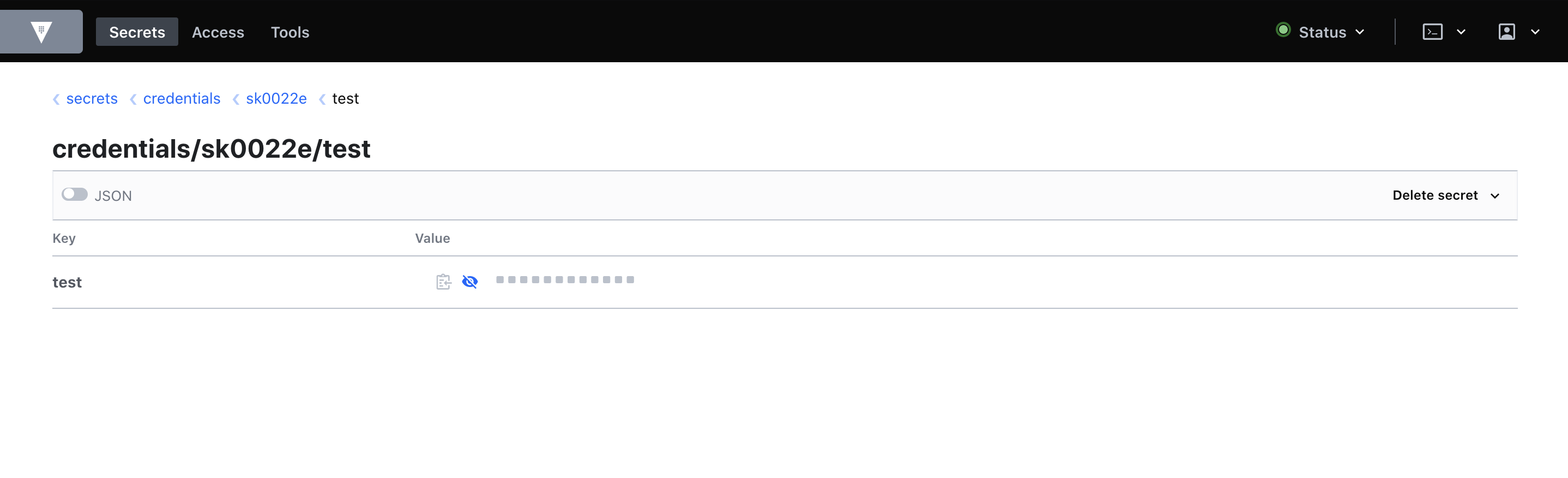
UTHPC shares all kinds of secrets with you by utilizing the secrets system of Vault. Under the path Secrets Engines :material-arow-right: Secrets Credentials <Your UT Username> <secret name>.
UTHPC administrator gives the secret name.
In the website it looks something like this:
In the command line tool you can just do the following command after having successfully authenticated:
vault kv get secrets/credentials/<username>/<secret name>
Credentials system rules¶
There are some rules you need to be aware of to use this system properly:
- Admins can't read, edit, delete or update the ’<secrets name>’ secret, only create it.
- Admins are only capable of writing a secret to ’<secret name>’ if the secret doesn't exist yet.
- Only users themselves can read and delete secrets. They can't write secrets themselves.
- If a secret exists, then the user needs to delete it before admins can write to it.
- System logs, audits, and validates all actions.
Important
You should always delete the secret after reading it. This is to prevent secrets from falling into wrong hands. Even though the chance is tiny, cleaning up any credentials laying around is always a good idea.
Send sensitive information to UTHPC¶
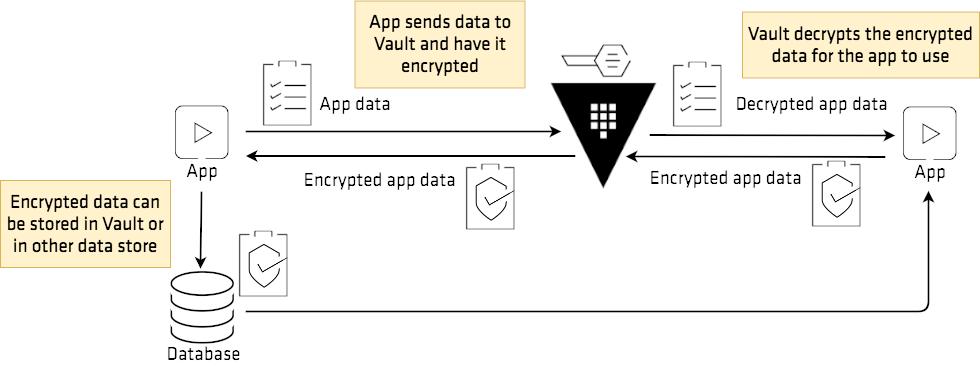
You can share sensitive information with UTHPC, utilizing the transit system of Vault. This system utilizes a secret to encrypt data, and based on policies, users can encrypt their data and only admins can decrypt data using the same key. Neither users or admins actually know the key used to encrypt/decrypt data.
It looks something like this on a picture, just instead of ’app’ there is ’user’ and ’admin’.
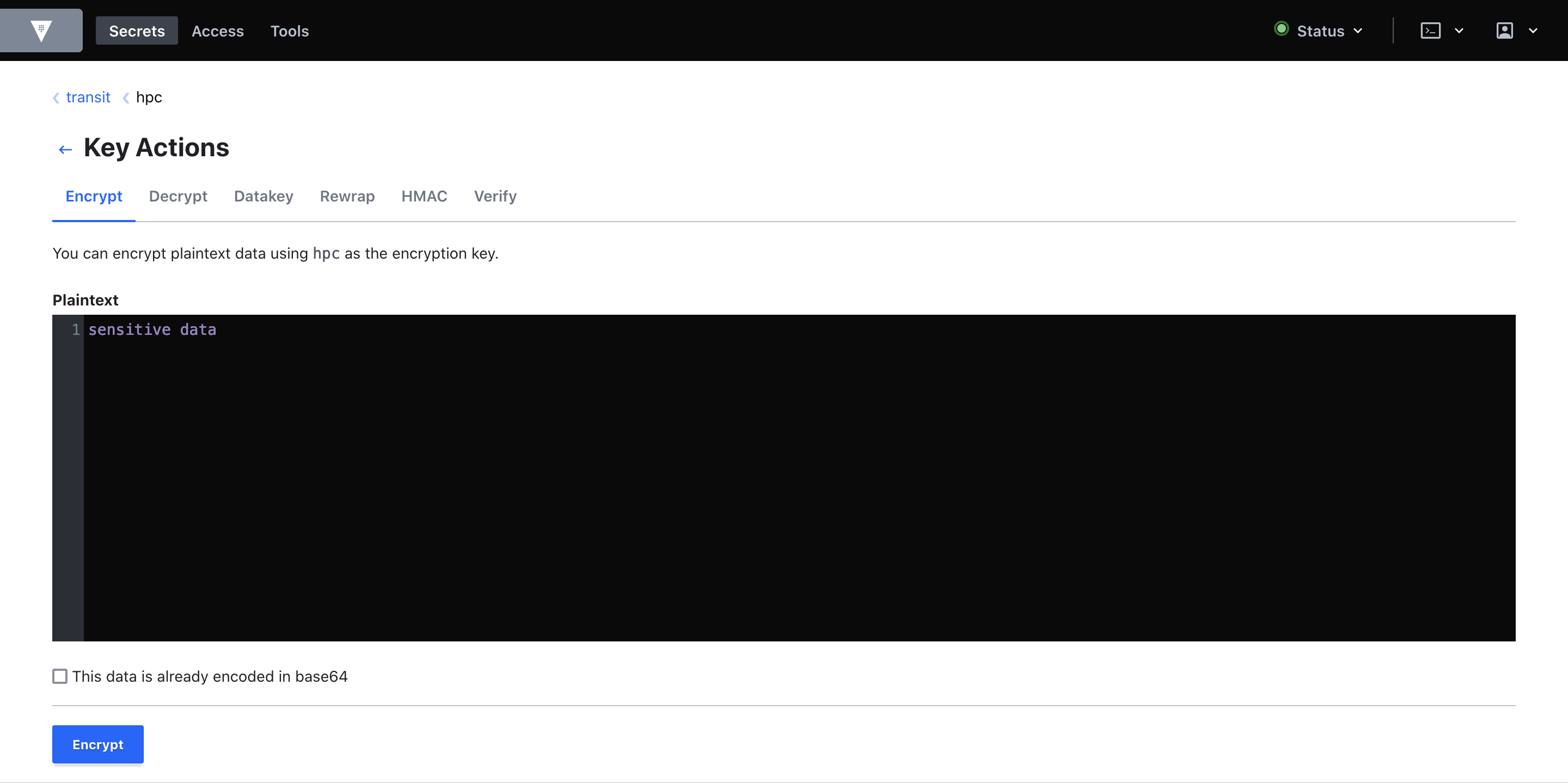
Using this system is fairly easy. When logged into the web UI of Vault, you need to go to ’transit’ ’hpc’. In there, choose ’encrypt’, copy your data into the text box, and press ’encrypt’.
After pressing ’encrypt’, you get a ciphertext in a small window. This is the data you can freely copy and share over insecure channels, as only UTHPC admins are capable of opening this.
When using the command line tool, you need to do the following instead:
vault write transit/encrypt/hpc plaintext="Sensitive data"
Key Value
--- -----
ciphertext vault:v1:f3X2gtoGBWszk4qJVyZtcpnuFUJgS9aJ1kILCYOfVw==
key_version 1
Important
The transit key is re-wrapped every two weeks, and only two versions are valid. This effectively means, that the ciphertext value is available for decryption only for one month. Afterwards you can't decrypt it.